Manual:Interface/OVPN
Summary
Standards:
Package: ppp
Currently unsupported OVPN feature:
- UDP mode
- LZO compression
- TLS authentication
- authentication without username/password
OVPN Client
Sub-menu: /interface ovpn-client
Properties
| Property | Description |
|---|---|
| add-default-route (yes | no; Default: no) | Whether to add OVPN remote address as a default route. |
| auth (md5 | sha1; Default: sha1) | Allowed authentication methods. |
| certificate (string | none; Default: none) | Name of the client certificate imported into certificate list. |
| cipher (aes128 | aes192 | aes256 | blowfish128; Default: blowfish128) | Allowed ciphers. |
| comment (string; Default: ) | Descriptive name of an item |
| connect-to (IP; Default: ) | Remote address of the OVPN server. |
| disabled (yes | no; Default: yes) | Whether interface is disabled or not. By default it is disabled. |
| mac-address (MAC; Default: ) | Mac address of OVPN interface. Will be auto generated if not specified. |
| max-mtu (integer; Default: 1500) | Maximum Transmission Unit. Max packet size that OVPN interface will be able to send without packet fragmentation. |
| mode (ip | ethernet; Default: ip) | Layer3 or layer2 tunnel mode (alternatively tun, tap) |
| name (string; Default: ) | Descriptive name of the interface. |
| password (string; Default: "") | Password used for authentication. |
| port (integer; Default: 1194) | Port to connect to. |
| profile (name; Default: default) | Used PPP profile. |
| user (string; Default: ) | User name used for authentication. |
Quick example
This example demonstrates how to set up OVPN client with username "test", password "123" and server 10.1.101.1
[admin@bumba] /interface ovpn-client> add connect-to=10.1.101.1 user=test password=123 disabled=no
[admin@bumba] /interface ovpn-client> print
Flags: X - disabled, R - running
0 name="ovpn-out1" mac-address=FE:7B:9C:F9:59:D0 max-mtu=1500 connect-to=10.1.101.1
port=1194 mode=ip user="test" password="123" profile=default certificate=none auth=sha1
cipher=blowfish128 add-default-route=no
OVPN Server
Sub-menu: /interface ovpn-server
This sub-menu shows interfaces for each connected OVPN clients.
An interface is created for each tunnel established to the given server. There are two types of interfaces in OVPN server's configuration
- Static interfaces are added administratively if there is a need to reference the particular interface name (in firewall rules or elsewhere) created for the particular user.
- Dynamic interfaces are added to this list automatically whenever a user is connected and its username does not match any existing static entry (or in case the entry is active already, as there can not be two separate tunnel interfaces referenced by the same name).
Dynamic interfaces appear when a user connects and disappear once the user disconnects, so it is impossible to reference the tunnel created for that use in router configuration (for example, in firewall), so if you need a persistent rule for that user, create a static entry for him/her. Otherwise it is safe to use dynamic configuration.
Note: in both cases PPP users must be configured properly - static entries do not replace PPP configuration.
Server configuration
Sub-menu: /interface ovpn-server server
Properties:
| Property | Description |
|---|---|
| auth (sha1 | md5; Default: sha1,md5) | Authentication methods that server will accept. |
| certificate (name | none; Default: none) | Name of the certificate that OVPN server will use. |
| cipher (aes128 | aes192 | aes256 | blowfish128; Default: aes128,blowfish128) | Allowed ciphers. |
| default-profile (name; Default: default) | Default profile to use. |
| enabled (yes | no; Default: no) | Defines whether OVPN server is enabled or not. |
| keepalive-timeout (integer | disabled; Default: 60) | Defines the time period (in seconds) after which the router is starting to send keepalive packets every second. If no traffic and no keepalive responses has came for that period of time (i.e. 2 * keepalive-timeout), not responding client is proclaimed disconnected |
| mac-address (MAC; Default: ) | Auto Generated MAC address of the server. |
| max-mtu (integer; Default: 1500) | Maximum Transmission Unit. Max packet size that OVPN interface will be able to send without packet fragmentation. |
| mode (ip | ethernet; Default: ip) | Layer3 or layer2 tunnel mode (alternatively tun, tap) |
| netmask (integer; Default: 24) | Subnet mask to be applied to client. |
| port (integer; Default: 1194) | Port to run server on. |
| require-client-certificate (yes | no; Default: no) | If set to yes, then server checks whether client's certificate belongs to the same certificate chain. |
[admin@bumba] /interface ovpn-server server set enabled=yes
[admin@bumba] /interface ovpn-server server set certificate=server
[admin@bumba] /interface ovpn-server server print
enabled: yes
port: 1194
mode: ip
netmask: 24
mac-address: FE:A5:57:72:9D:EC
max-mtu: 1500
keepalive-timeout: 60
default-profile: default
certificate: server
require-client-certificate: no
auth: sha1,md5
cipher: blowfish128,aes128
Warning: It is very important that the date on the router is within the range of the installed certificate's date of expiration. To overcome any certificate verification problems, enable NTP date synchronization on both server and client.
Monitoring
Monitor command can be used to monitor the status of the tunnel on both client and server.
[admin@dzeltenais_burkaans] /interface ovpn-server monitor 0
status: "connected"
uptime: 17m47s
idle-time: 17m47s
user: "test"
caller-id: "10.1.101.18:43886"
mtu: 1500
Read-only properties
| Property | Description |
|---|---|
| status () | Current status. Value other than "connected" indicates that there are some problems establishing tunnel. |
| uptime (time) | Elapsed time since tunnel was established. |
| idle-time (time) | Elapsed time since last activity on the tunnel. |
| user (string) | Username used to establish the tunnel. |
| mtu (integer) | Negotiated and used MTU |
| caller-id (IP:ID) | Source IP and Port of client. |
Application Examples
Setup Overview
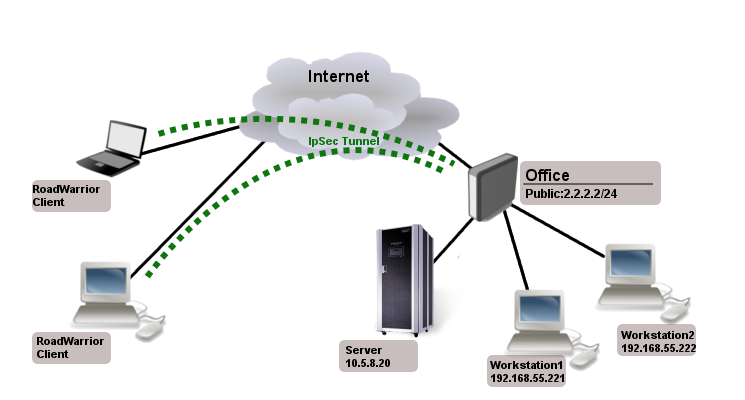
Assume that Office public IP address is 2.2.2.2 and we want two remote OVPN clients to have access to 10.5.8.20 and 192.168.55.0/24 networks behind office gateway.
Creating Certificates
All certificates can be created on RadioOS server using certificate manager. See example >>.
For simplest setup you need only ovpn server certificate.
Server Config
First step is to create ip pool from which client addresses will be assigned and some users
/ip pool add name=ovpn-pool range=192.168.77.2-192.168.77.254 /ppp profile add name=ovpn local-address=192.168.77.1 remote-address=ovpn-pool /ppp secret add name=client1 password=123 profile=ovpn add name=client2 password=234 profile=ovpn
Assume that server certificate is already created and named "server"
/interface ovpn-server server set enabled=yes certificate=server
Client Config
RadioOS client
Since RadioOS does not support route-push you need to add manually which networks you want to access over the tunnel.
/interface ovpn-client add name=ovpn-client1 connect-to=2.2.2.2 user=client1 password=123 disabled=no /ip route add dst-address=10.5.8.20 gateway=ovpn-client1 add dst-address=192.168.55.0/24 gateway=ovpn-client1 /ip firewall nat add chain=srcnat action=masquerade out-interface=ovpn-client1
Linux Client config
dev tun proto tcp-client remote 2.2.2.2 1194 tls-client user nobody group nogroup #comp-lzo # Do not use compression. # More reliable detection when a system loses its connection. ping 15 ping-restart 45 ping-timer-rem persist-tun persist-key mute-replay-warnings verb 3 cipher BF-CBC auth SHA1 pull auth-user-pass auth.cfg
The file auth.cfg holds your username/password combination. On the first line must be the username and on the second line your password.
client2 234
[ Top | Back to Content ]