Manual:Internet access from VRF with NAT
Packages required: routing-test, mpls-test, RadioOS version 3.28+
MPLS Per-VRF NAT for internet access to L3VPNs
Abstract
This article will describe the basic configuration of how to provide internet access to L3VPN customers in an MPLS infrastructure. It has been tested with RadioOS version 3.28 with mpls-test and routing-test. This article assumes basic knowledge of MPLS operation as well as knowledge of NAT and routing.
Requirements
The concepts in this article requires at least one routable public ip address per VRF that needs to have internet access. It also requires you to have a dedicated PE-router to be placed between your internet-connected router and the MPLS network in order to do the actuall NAT translation before the data is transmitted to the internet-facing router. This article does not require you to have your own AS, although it may be convenient, just as long as you have the routable public IP addresses to spare for your customers.
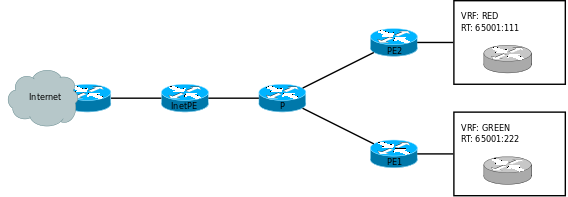
Example topology
In this example topology we have two customers, RED and GREEN, who both reside in a separate VRF. Their LAN addressing is of no concern to this setup, and could possibly overlap. They receive internet access on the InetPE router. This design is not an actual MPLS network, but just a simple illustration of the basic concept.
InetPE configuration
We assume that the example network here has a public network of 1.1.1.0/24. The link between the InetPE and the actual internet gateway is 1.1.1.0/30, and 1.1.1.16/28 is assigned for VRFs terminating here. A default route to the internet gateway exists on the InetPE in some form, pointing to 1.1.1.1, and 1.1.1.1 should have a route to 1.1.1.16/28 via 1.1.1.2 (the InetPE).
VRF configuration
The VRFs are configured like this:
/ip route vrf add routing-mark=RED route-distinguisher=65001:111 import-route-targets=65001:111 \ export-route-targets=65001:111 disabled=no /ip route vrf add routing-mark=GREEN route-distinguisher=65001:222 import-route-targets=65001:222 \ export-route-targets=65001:222 disabled=no /routing bgp instance vrf add routing-mark=RED redistribute-static=yes instance=default /routing bgp instance vrf add routing-mark=GREEN redistribute-static=yes instance=default
Default Route
To add a default route, the following commands should be used:
/ip route add routing-mark=RED dst-address=0.0.0.0/0 gateway=1.1.1.1@main /ip route add routing-mark=GREEN dst-address=0.0.0.0/0 gateway=1.1.1.1@main
Notice the @main part. This indicates that the address 1.1.1.1 should be resolved on the main routing table instead of inside the VRF routing table.
NAT
In this step, we will source NAT the traffic from the RED VRF to the address 1.1.1.16 and the GREEN VRF to 1.1.1.17. This requires both a NAT entry and a MANGLE entry, since the return traffic does not automatically go back into the correct VRF.
- NAT:
/ip firewall nat add action=src-nat chain=srcnat out-interface=ether1 routing-mark=RED \ to-addresses=1.1.1.16 disabled=no /ip firewall nat add action=src-nat chain=srcnat out-interface=ether1 routing-mark=GREEN \ to-addresses=1.1.1.17 disabled=no
- MANGLE:
/ip firewall mangle add chain=prerouting action=mark-routing disabled=no dst-addres=1.1.1.16 \ new-routing-mark=RED passthrough=yes /ip firewall mangle add chain=prerouting action=mark-routing disabled=no dst-address=1.1.1.17 \ new-routing-mark=GREEN passthrough=yes
Further design considerations
There are several ways you could enhance this design. You could consider breaking out internet access to a separate RT, allowing you a little more flexibility with the internet routes. I have yet to find out how to do this without a default route that points to a next-hop router, eg. if you want to terminate the VRF's on a box with full BGP feed. If you discover, please update this Wiki article.
Conclusion
This configuration is enough to get simple src-nat working. You may want to fine tune these rules to fit into your setup. Dst-nat is not covered by this guide, but should be simple to set up as long as you remember to set up the corresponding mangle rules. It has not been thoroughly tested, so I cannot say what kind of performance you might expect from this.